Understanding SIP Trunking with Asterisk
In the world of Voice over Internet Protocol (VoIP), a SIP trunk asterisk setup is a popular and powerful solution. It allows you to connect your Asterisk phone system to the public switched telephone network (PSTN) using the Session Initiation Protocol (SIP). This eliminates the need for traditional physical phone lines, offering cost savings and increased flexibility.
What is a SIP Trunk?
A SIP trunk is a virtual phone line that utilizes the internet to transmit voice and other unified communications data. Instead of relying on physical copper wires, SIP trunks use your existing broadband connection. A sip trunk asterisk configuration enables your Asterisk PBX to make and receive calls over the internet.
Why Choose SIP Trunking for Asterisk?
Asterisk is an open-source PBX software that provides a robust and customizable platform for managing your business communications. Combining Asterisk with SIP trunking creates a powerful and cost-effective solution. A key advantage is the ability to scale your phone system easily. Adding or removing channels (concurrent calls) is often as simple as adjusting your SIP trunk subscription.
Benefits of Using a SIP Trunk with Asterisk
- Cost Savings: SIP trunking can significantly reduce phone costs by eliminating the need for traditional phone lines.
- Scalability: Easily add or remove channels as your business needs change.
- Flexibility: SIP trunks can be used from anywhere with an internet connection.
- Advanced Features: SIP trunking often comes with advanced features like call forwarding, caller ID, and voicemail.
- Integration: Seamless integration with Asterisk and other VoIP applications.
Choosing the Right SIP Trunk Provider for Asterisk
Selecting the right asterisk sip trunk provider is crucial for a successful VoIP implementation. Not all providers are created equal, and factors like reliability, pricing, and features can vary significantly. Carefully evaluate your options to find a provider that meets your specific needs.
Key Factors to Consider
- Reliability: Look for providers with a proven track record of uptime and reliable service.
- Pricing: Compare pricing models, including per-channel, metered, and unlimited options. Understanding the sip trunk pricing asterisk is essential.
- Features: Determine the features you need, such as caller ID, call forwarding, and direct inward dialing (DID) numbers.
- Support: Ensure the provider offers adequate technical support, especially during the initial asterisk sip trunk setup.
- Compatibility: Verify that the SIP trunk provider is compatible with your version of Asterisk.
Comparing SIP Trunk Providers
Consider these factors when comparing providers for your asterisk sip trunk:
- Service Level Agreements (SLAs): Look for providers with guaranteed uptime and service quality.
- Geographic Coverage: Ensure the provider offers service in your desired geographic locations.
- Customer Reviews: Read online reviews and testimonials to get an idea of the provider's reputation.
- Trial Periods: Some providers offer trial periods, allowing you to test their service before committing.
Features to Look for in a SIP Trunk
- Caller ID: The ability to display your phone number to recipients.
- Call Forwarding: Automatically forward calls to another number.
- Direct Inward Dialing (DID): Assign individual phone numbers directly to extensions.
- E911 Support: Emergency services support, allowing callers to reach emergency services.
- CNAM Lookup: Retrieve the name associated with a phone number.
Setting Up Your SIP Trunk in Asterisk
This section outlines the steps required for setting up a sip trunk in asterisk. We'll cover configurations using both
chan_sip and pjsip, the two main SIP channel drivers for Asterisk.Prerequisites: Software and Accounts
Before you begin, ensure you have the following:
- An installed and configured Asterisk PBX.
- An account with a SIP trunk provider.
- The necessary credentials from your provider (SIP username, password, server address).
- A basic understanding of Asterisk configuration files.
Step-by-Step Configuration Guide: Using chan_sip
The
chan_sip channel driver is the older, more established option. However, it's gradually being replaced by pjsip. Here's how to configure a sip trunk asterisk using chan_sip:- Edit
sip.conf: Open thesip.conffile (usually located in/etc/asterisk/) and add the following configuration:
sip.conf
1[general]
2context=default
3allowguest=no
4
5[your_sip_trunk_name] ; Replace with a descriptive name
6type=friend
7host=your_sip_provider_host ; Replace with your provider's SIP server address
8username=your_sip_username ; Replace with your SIP username
9secret=your_sip_password ; Replace with your SIP password
10qualify=yes
11insecure=invite,port
12context=from-trunk ; Define the context for incoming calls
13disallow=all
14allow=ulaw
15allow=alaw
16- Create a Context: In
extensions.conf(usually located in/etc/asterisk/), create a context to handle incoming calls from the SIP trunk. For example:
extensions.conf
1[from-trunk]
2exten => _X.,1,Dial(SIP/your_extension_number/${EXTEN}) ; Replace your_extension_number
3- Reload Asterisk: Reload the Asterisk configuration:
CLI
1asterisk -rx "sip reload"
2asterisk -rx "dialplan reload"
3Step-by-Step Configuration Guide: Using pjsip
The
pjsip channel driver is the recommended option for new Asterisk installations. It offers improved performance and security features. Here's how to configure a sip trunk asterisk using pjsip:- Create an Endpoint: Create an endpoint in
pjsip.conf(usually located in/etc/asterisk/pjsip.conf):
pjsip.conf
1[your_sip_trunk_name](!) ; Replace with a descriptive name
2type=endpoint
3context=from-trunk ; Define the context for incoming calls
4disallow=all
5allow=ulaw,alaw
6aors=your_sip_trunk_name
7
8[your_sip_trunk_name](your_sip_trunk_name) ; Replace with the same name as the endpoint
9type=aor
10contact=sip:your_sip_username@your_sip_provider_host ; Replace credentials
11
12[your_sip_trunk_name](!) ; Replace with a descriptive name
13type=auth
14auth_type=userpass
15password=your_sip_password ; Replace with your SIP password
16username=your_sip_username ; Replace with your SIP username
17
18[your_sip_trunk_name](your_sip_trunk_name) ; Replace with the same name as the endpoint
19type=registration
20contact_user=your_sip_username ; Replace with your SIP username
21client_uri=sip:your_sip_username@your_sip_provider_host ; Replace credentials
22server_uri=sip:your_sip_provider_host ; Replace with your provider's SIP server address
23auth=your_sip_trunk_name
24retry_interval=60
25forbidden_retry_interval=300
26- Create a Context: In
extensions.conf, create a context to handle incoming calls, similar to thechan_sipexample.
extensions.conf
1[from-trunk]
2exten => _X.,1,Dial(PJSIP/your_extension_number/${EXTEN}) ; Replace your_extension_number
3- Reload Asterisk: Reload the Asterisk configuration:
CLI
1asterisk -rx "pjsip reload"
2asterisk -rx "dialplan reload"
3Testing Your SIP Trunk Configuration
After configuring your asterisk sip trunk, test it by making and receiving calls. Use the Asterisk CLI to monitor SIP traffic and troubleshoot any issues.
CLI
1asterisk -rx "pjsip show registrations" ; Check PJSIP registration status
2asterisk -rx "sip show peers" ; Check chan_sip peer status (if using chan_sip)
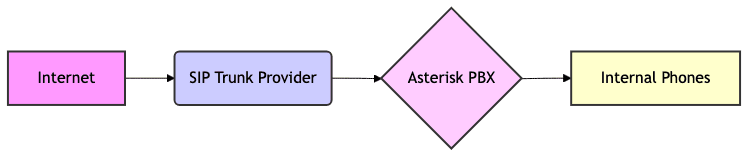
3Here's a Mermaid diagram that visualizes the SIP Trunk Asterisk connection:
Advanced Configurations and Troubleshooting
Once you have a basic sip trunk asterisk setup, you can explore advanced configurations and address common issues.
Handling NAT Traversal and Firewalls
Network Address Translation (NAT) and firewalls can interfere with SIP traffic. Ensure your firewall allows UDP traffic on ports 5060 (SIP) and the RTP port range (typically 10000-20000). Use the
externip and localnet settings in sip.conf (for chan_sip) or nat and rewrite_contact settings in pjsip.conf to help Asterisk correctly identify its public IP address.Configuring QoS for Optimal Call Quality
Quality of Service (QoS) prioritizes voice traffic over other network traffic. Configure QoS on your router to give SIP and RTP packets higher priority. This can improve call quality, especially on networks with high traffic.
Troubleshooting Common SIP Trunk Issues
- Registration Problems: Verify your SIP credentials and server address are correct. Check your firewall settings.
- One-Way Audio: This is often caused by NAT issues. Ensure your
externipandlocalnetsettings are correctly configured. - Call Drops: Investigate network connectivity issues or problems with your SIP trunk provider.
- Codec Mismatches: Ensure your Asterisk and SIP trunk provider support compatible codecs.
Implementing Failover for High Availability
To ensure high availability, you can configure a failover system. This involves having a backup SIP trunk or a secondary Asterisk server that can take over if the primary system fails. Consider using DNS SRV records for automatic failover.
Integrating Asterisk with Your SIP Trunk Provider
Successfully integrating asterisk with your chosen sip trunk provider ensures seamless communication and efficient management of your VoIP system.
Account Setup and Credentials
After signing up with a SIP trunk provider, you will receive essential credentials, including:
- SIP Username/Authentication ID
- SIP Password
- SIP Server Address/Domain
Ensure to securely store these credentials, as they are crucial for connecting Asterisk to your provider's network. Use an
open-source password manager
for added security.Number Porting Considerations
If you're switching from a traditional phone system, you'll likely want to port your existing phone numbers to your new SIP trunk. This process, known as number porting, can take time, so start the process well in advance. Contact your SIP trunk provider to initiate the porting process.
Understanding Billing and Usage
Different SIP trunk providers offer various billing models, such as:
- Metered: You pay for the actual minutes used.
- Unlimited: You pay a fixed monthly fee for unlimited calling.
- Bundled: A combination of metered and unlimited minutes.
Understand the pricing structure of your provider and monitor your usage to avoid unexpected charges.
Security Best Practices for Asterisk SIP Trunks
Securing your asterisk sip trunk is paramount to prevent fraud, unauthorized access, and service disruptions.
Authentication and Authorization
- Strong Passwords: Use strong, unique passwords for your SIP accounts and Asterisk system.
- IP Address Restrictions: Restrict access to your Asterisk system to specific IP addresses or networks.
- SIP Registration: Require SIP registration for all devices and trunks.
Encryption and SRTP
Use Secure Real-time Transport Protocol (SRTP) to encrypt voice traffic. This prevents eavesdropping and protects the privacy of your calls. Configure SRTP in your
sip.conf or pjsip.conf file.Firewall Rules and Network Security
- Firewall Configuration: Configure your firewall to allow only necessary traffic to your Asterisk system.
- Intrusion Detection Systems (IDS): Implement an IDS to detect and prevent unauthorized access attempts.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
Monitoring and Management of your Asterisk SIP Trunk
Effective monitoring is essential for maintaining a stable and reliable sip trunk asterisk configuration. By continuously observing your system, you can proactively identify and address potential issues before they impact your communications.
Real-time Monitoring Tools
Utilize real-time monitoring tools to track the status of your SIP trunks, call volumes, and system performance. Some popular tools include:
- Asterisk CLI: Use the Asterisk command-line interface to monitor SIP traffic and system status.
- Third-Party Monitoring Solutions: Explore third-party monitoring solutions that provide comprehensive insights into your Asterisk system.
Asterisk Manager Interface (AMI)
The Asterisk Manager Interface (AMI) allows external applications to monitor and control Asterisk. You can use AMI to build custom monitoring dashboards and automate management tasks.
Log Analysis
Regularly analyze Asterisk log files to identify potential issues, such as registration failures, call drops, and security threats. Tools like
grep, awk, and log management systems can help you efficiently analyze log data.Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ