STUN VoIP: The Essential Guide to NAT Traversal and Call Quality (2025)
Introduction to STUN VoIP
Voice over IP (VoIP) has revolutionized communication by delivering high-quality voice calls over the internet. However, one persistent challenge remains: Network Address Translation (NAT). NAT, while great for network security and IP conservation, often disrupts VoIP signaling and media streams, leading to poor call quality and connectivity issues. Enter the STUN protocol—a key player in modern stun voip deployments. STUN (Session Traversal Utilities for NAT) enables SIP devices to discover their public IP address and port mappings, making NAT traversal possible. In this guide, we’ll demystify stun voip, explore practical configurations, and help you optimize your VoIP network for flawless performance.
Understanding NAT and Its Challenges for VoIP
What is NAT?
Network Address Translation (NAT) is a method used by routers to translate private, internal IP addresses into a public IP address for communication with external networks. While NAT provides security and IP address economy, it complicates real-time communication protocols like VoIP.
How NAT Affects VoIP Communications
VoIP relies on the Session Initiation Protocol (SIP) and Real-time Transport Protocol (RTP) for call signaling and media transmission. NAT obscures the actual device IP, causing SIP messages to advertise inaccessible private addresses. This mismatch can result in:
- One-way or no audio (RTP streams blocked)
- SIP registration failures
- Problems with call setup and teardown
- Inability to receive incoming connections
Common NAT-Related VoIP Issues
- One-way audio: RTP packets from the callee can't traverse NAT to reach the caller.
- Registration failures: SIP devices fail to register with the SIP server due to mismatched IPs.
- Dropped calls: NAT timeouts or port changes break media streams.
NAT Traversal Flow (Mermaid Diagram)
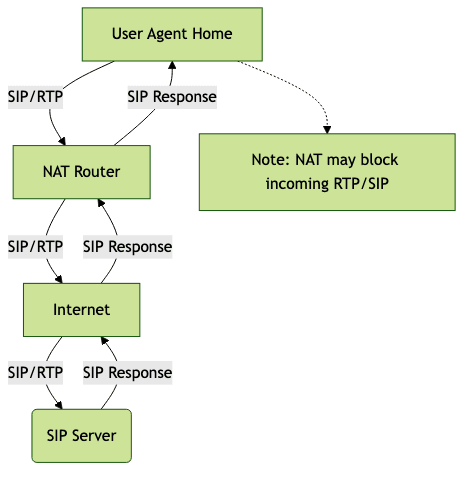
What is STUN in VoIP?
Definition of STUN (Session Traversal Utilities for NAT)
STUN is a lightweight protocol that allows SIP devices and VoIP clients to determine their public IP address and port as seen by external servers. This is essential for establishing direct peer-to-peer voice sessions across NAT boundaries.
How STUN Works
- The SIP device sends a STUN request to a STUN server on the public internet.
- The STUN server replies with the public IP and port from which the request originated.
- The device uses this information in SIP messages, enabling endpoints to reach each other despite NAT.
STUN, TURN, and ICE: Key Differences
- STUN: Discovers public IP/port, enabling direct connections. Ideal for simple NATs.
- TURN: Relays traffic through a server when direct connection is impossible (e.g., symmetric NAT).
- ICE (Interactive Connectivity Establishment): Orchestrates STUN, TURN, and other methods to maximize connectivity.
Emphasis on STUN VoIP
In stun voip setups, STUN offers a low-latency, bandwidth-efficient NAT traversal solution when compared to TURN. ICE builds on STUN but is especially valuable in complex, multi-device environments.
How STUN Improves VoIP Call Quality
Discovering Public IP and Port Mapping
STUN empowers SIP devices in stun voip networks to automatically discover their public-facing IP address and port mappings. This ensures that RTP audio streams and SIP signaling can reach the device, bypassing NAT-induced issues.
Resolving Audio and Connectivity Issues
By advertising the correct public address, STUN eliminates common one-way audio and registration errors. It supports NAT keep-alive mechanisms, reducing the risk of session drops due to NAT timeouts.
Limitations of STUN
- Symmetric NAT: STUN cannot always traverse symmetric NAT, where port mappings are unpredictable.
- Provider Compatibility: Some VoIP providers and firewalls block STUN traffic, requiring alternatives like TURN or session border controllers (SBCs).
Setting Up STUN for VoIP Devices
STUN VoIP Configuration Example
Configuring STUN on SIP phones and adapters is straightforward. Below are practical examples for Yealink, Grandstream, and Linksys/Sipura devices.
Yealink IP Phone (Web GUI)
- Login to the Yealink web interface.
- Navigate to Account > Advanced.
- Set STUN Server to a public server (e.g.,
stun.l.google.com:19302). - Enable NAT Traversal and set Keep Alive Interval (e.g., 30 seconds).
- Click Confirm to save.
Grandstream (Web GUI)
- Go to Accounts > Network Settings.
- Enter STUN Server (e.g.,
stun1.voiceeclipse.net). - Set NAT Traversal to STUN.
- Adjust Keep Alive Interval as needed.
- Save and reboot the device.
Linksys/Sipura (INI Configuration)
1nat_enable: 1
2stun_enable: 1
3stun_server: "stun.l.google.com:19302"
4nat_keepalive_interval: 30
5outbound_proxy: ""
6Best Practices for STUN VoIP Setup
- Choosing a Public STUN Server: Use reliable, low-latency servers (Google, Twilio, or your provider).
- Outbound Proxy: Use only if your provider or firewall requires it; otherwise, prefer direct STUN.
- NAT Keep-Alive: Set intervals between 20-60 seconds to maintain port mappings.
- Port Forwarding: Forward SIP (5060 UDP/TCP) and RTP (usually 10000-20000 UDP) ports when possible.
- Dynamic DNS: For remote/home offices, use DDNS to handle changing public IPs.
Advanced STUN VoIP Scenarios
Remote Offices and Home VoIP
STUN is ideal for small/home offices where a dedicated SBC is overkill. It enables plug-and-play SIP phones and adapters to function reliably with cloud PBXs.
Combining STUN with ICE
For multi-device or mobile environments (e.g., WebRTC clients), combine STUN with ICE for dynamic NAT traversal. ICE orchestrates candidate gathering and connectivity checks across STUN, TURN, and direct paths.
When to Use SBC Instead of STUN
Large enterprises or providers may require a Session Border Controller (SBC) for advanced NAT traversal, security, and interoperability. SBCs can manage SIP signaling, media relaying, and enforce policies beyond what stun voip can offer alone.
STUN vs SBC Architecture (Mermaid Diagram)
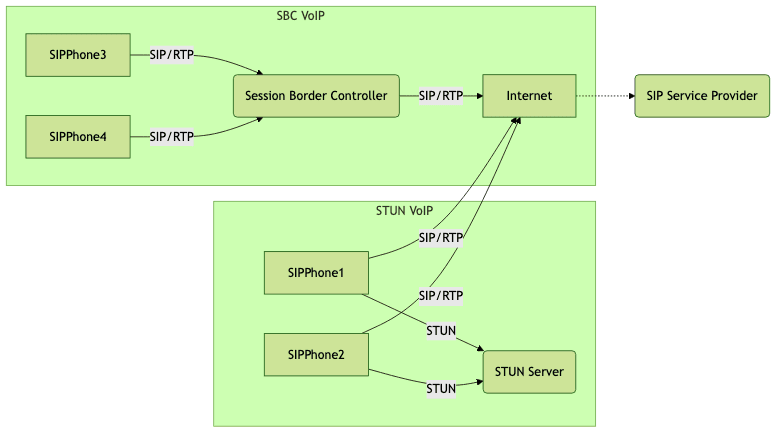
Troubleshooting Common STUN VoIP Problems
Diagnosing Issues
- One-way audio: Check firewall rules, ensure correct STUN server.
- Registration failures: Verify NAT keep-alive and public IP mapping.
- Dropped calls: Inspect NAT timeout intervals and port forwarding.
Tools and Commands
Use
stunclient or similar utilities to verify STUN operation.1stunclient stun.l.google.com 19302
2Expected output:
1STUN client version 1.2.0
2Primary: Opened UDP socket to 74.125.142.127:19302
3MappedAddress: 203.0.113.45:54321
4NAT Type: Full Cone
5Example Error Messages & Resolutions
SIP Registration Timeout: Check STUN config and keep-alive interval.No audio received: Confirm RTP ports are open and mapped by NAT.STUN server unreachable: Test with a different public STUN server.
STUN VoIP Security and Privacy Considerations
Exposing SIP devices via STUN introduces certain risks:
- Device Discovery: Public IPs and ports are revealed, potentially exposing devices.
- UDP Vulnerabilities: NAT traversal relies on UDP, which is susceptible to spoofing and DoS attacks.
Mitigation Best Practices
- Restrict allowed IPs and protocols at the firewall.
- Use strong SIP authentication credentials.
- Regularly update firmware on SIP devices.
- Use dynamic DNS securely—protect DDNS credentials and monitor for unauthorized changes.
Conclusion: Maximizing VoIP Reliability with STUN
STUN is a powerful tool for overcoming NAT traversal in VoIP networks, enabling clear, reliable calls across home, office, and remote environments. Proper stun voip configuration ensures seamless SIP registration, optimal audio quality, and robust connectivity. Combined with best practices and security controls, STUN empowers your VoIP deployment for success in 2025 and beyond.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ