Introduction to Protocol VoIP
Voice over IP (VoIP) has revolutionized digital communication by enabling real-time voice and multimedia sessions over IP networks. At the heart of this technology is a collection of protocols—rules and conventions that govern how voice, video, and data packets traverse the internet. The term protocol VoIP refers to these essential standards, such as SIP, RTP, and H.323, which orchestrate everything from call signaling and media transport to security and quality assurance.
Understanding protocol VoIP is fundamental for network engineers, developers, and IT professionals designing or maintaining IP telephony systems. Mastery of these protocols ensures reliable, interoperable, and secure communications, which are critical as businesses worldwide continue to migrate from legacy telephony to advanced IP-based solutions in 2025.
The Role of Protocols in VoIP Communication
VoIP protocols operate across several layers, each with distinct responsibilities, mirroring and extending the classic OSI model. Protocols in VoIP manage signaling (call setup and teardown), media transport (audio/video streams), and security (encryption, authentication).
While the OSI model provides a conceptual framework, VoIP protocol stacks are tailored to real-time transmission and interoperability:
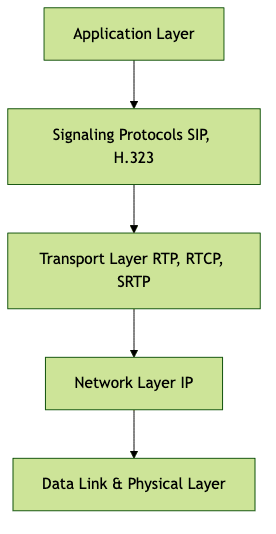
This layered approach allows protocol VoIP systems to efficiently route, secure, and control voice and video data, supporting everything from simple peer-to-peer calls to complex enterprise deployments.
Core Types of VoIP Protocols
Signaling Protocols
Signaling protocols are responsible for establishing, modifying, and terminating multimedia sessions. The most prominent signaling protocols in 2025 include:
- SIP (Session Initiation Protocol): The de facto standard, SIP is text-based, modular, and highly extensible. SIP messages initiate, manage, and end sessions between endpoints, supporting features like presence, registration, and NAT traversal. Its widespread adoption is due to its simplicity and integration with web technologies.
- H.323: Once the dominant standard for VoIP and video conferencing, H.323 is more complex and binary-oriented. It bundles signaling, control, and media transport in an all-in-one suite. While its popularity has waned in favor of SIP, H.323 remains relevant in legacy systems and some large enterprise and service provider networks. SIP vs H.323 continues to be a key protocol comparison in VoIP planning.
- MGCP (Media Gateway Control Protocol): MGCP acts as a master/slave protocol, allowing external call agents to control media gateways within a VoIP network. It is commonly used in carrier and hybrid environments.
- SCCP (Skinny Client Control Protocol): Proprietary to Cisco, SCCP is used for communication between Cisco IP phones and call managers.
- IAX (Inter-Asterisk eXchange): Designed for Asterisk PBXs, IAX efficiently handles signaling and media over a single channel, making it ideal for trunking between VoIP servers and overcoming NAT issues.
Media Transport and Control Protocols
Once a call is established, media transport and control protocols take over:
- RTP (Real-Time Transport Protocol): RTP transfers audio, video, and other real-time data. It adds timestamps and sequence numbers for synchronization and jitter compensation. Here’s a simplified RTP packet structure in pseudocode:
1class RTPPacket:
2 def __init__(self, version, payload_type, sequence_number, timestamp, ssrc, payload):
3 self.version = version # RTP version
4 self.payload_type = payload_type # Codec type
5 self.sequence_number = sequence_number # Packet sequence
6 self.timestamp = timestamp # Media timestamp
7 self.ssrc = ssrc # Source identifier
8 self.payload = payload # Encoded audio/video
9- RTCP (RTP Control Protocol): RTCP works alongside RTP, monitoring transmission quality, providing feedback on packet loss and jitter, and enabling synchronization among streams.
- SRTP (Secure RTP): For secure communications, SRTP encrypts RTP payloads and provides message authentication, crucial for preventing eavesdropping and tampering in sensitive environments.
Protocol VoIP Stack: How It All Works Together
A typical VoIP call involves multiple protocols working in concert. Here’s how a SIP-based call might flow:
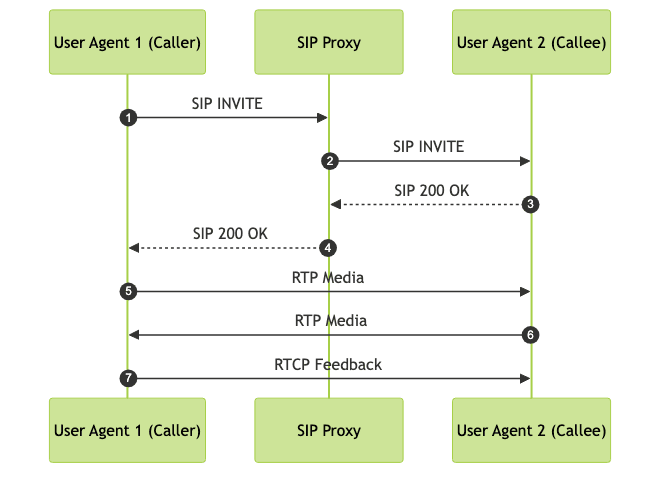
Real-world example: When Alice calls Bob using a SIP softphone, the SIP protocol manages the call setup through several message exchanges. Once accepted, RTP streams carry voice packets, while RTCP monitors transmission quality. If security is required, SRTP encrypts the voice stream end-to-end.
Protocol VoIP Security Considerations
VoIP is susceptible to security threats such as eavesdropping, spoofing, and denial-of-service attacks. To counter these, protocol VoIP implementations employ security protocols like:
- SRTP: Encrypts media streams, protecting confidentiality and integrity.
- TLS (Transport Layer Security): Secures signaling protocols (e.g., SIP over TLS), encrypting session initiation messages.
- S/MIME: Signs and optionally encrypts SIP message bodies for end-to-end security.
Common vulnerabilities include insecure endpoints, weak authentication, and unencrypted signaling. Best practices include:
- Always using SRTP and TLS where possible
- Strong endpoint authentication
- Regular protocol and firmware updates
- Network segmentation and strict firewall rules
Comparing Popular VoIP Protocols
SIP vs H.323
- SIP Pros: Simpler, more flexible, easier to debug, and better support for NAT/firewalls. Large ecosystem and open standards.
- H.323 Pros: Mature, reliable in large deployments, integrated media control.
- Cons: H.323 is complex and less flexible; SIP may need additional protocols for advanced features.
- Scenarios: SIP dominates modern enterprise and cloud VoIP; H.323 persists in legacy and some video conferencing systems.
RTP vs SRTP
- RTP: High performance, but unencrypted.
- SRTP: Adds confidentiality and integrity, essential for secure communications.
Selection Criteria for Businesses
- Security requirements
- Interoperability with existing systems
- Support for desired codecs and features
- Vendor ecosystem and community support
Implementation Best Practices for Protocol VoIP
- Interoperability: Use open standards (SIP, RTP) and verify compatibility between endpoints and gateways. Avoid vendor lock-in.
- Troubleshooting: Employ tools like Wireshark to analyze SIP and RTP traffic. Look for signaling errors, codec mismatches, and network issues.
- QoS and Bandwidth: Prioritize VoIP traffic using DiffServ or VLANs. Provision adequate bandwidth for concurrent calls, considering codec choice and overhead.
- Monitoring: Deploy RTCP-based monitoring and SNMP traps for real-time diagnostics. Use dashboards to visualize call quality metrics and protocol events.
- Diagnostics: Regularly test call setup, media path, and failover scenarios. Implement logging and alerting for protocol anomalies or security incidents.
Conclusion
Understanding protocol VoIP is vital for building robust, secure, and scalable IP telephony systems in 2025. As standards evolve, the focus is shifting toward enhanced security, better interoperability, and seamless integration with emerging technologies like WebRTC. Staying current with VoIP protocol developments ensures future-proof, high-quality communication solutions.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ