What is SIP in Networking? Complete Guide to Session Initiation Protocol (2025)
Introduction to SIP in Networking
In the ever-evolving landscape of digital communications, Session Initiation Protocol (SIP) plays a pivotal role in enabling real-time, multimedia interactions across networks. As organizations transition from traditional telephony to IP-based communication, understanding what SIP is in networking has become critical for IT professionals, developers, and network engineers. SIP serves as the backbone for Voice over IP (VoIP), video conferencing, instant messaging, and unified communications, making it a foundational signaling protocol in modern enterprise and service provider environments.
This guide provides a deep dive into SIP: its definition, architecture, message flow, comparison with other protocols, security considerations, and practical deployment tips. Whether you’re building scalable VoIP solutions, integrating video calling into your applications, or ensuring secure communications, this article will equip you with the essential knowledge of SIP in networking for 2025.
What is SIP?
Session Initiation Protocol (SIP) is a standardized application layer protocol used to initiate, manage, and terminate real-time multimedia sessions over IP networks. Defined by the Internet Engineering Task Force (IETF) in RFC 3261, SIP is crucial for establishing sessions involving voice, video, chat, and even gaming applications.
As a signaling protocol, SIP is responsible solely for setting up, modifying, and tearing down communication sessions. It does not handle the actual transmission of media (voice or video data)—that’s typically managed by protocols like RTP (Real-time Transport Protocol). Instead, SIP negotiates session parameters, manages user presence, and handles registration and authentication within the network.
SIP’s significance in networking is evident in its widespread adoption for VoIP and multimedia communication. Its text-based, flexible design allows easy integration with existing Internet protocols (HTTP, SMTP), and its extensibility has enabled rapid innovation in unified communications platforms.
In summary, SIP is the signaling protocol that powers modern IP telephony, providing the mechanisms for users and devices to find each other, establish connections, and manage sessions across diverse network environments.
SIP Architecture and Core Components
SIP employs a distributed client-server architecture, with various components working together to facilitate communication sessions. Here’s an overview of the essential elements:
- User Agent (UA): The endpoint device or software (such as a VoIP phone, softphone, or conferencing client) that initiates and receives SIP requests. Each UA acts as both a User Agent Client (UAC) and User Agent Server (UAS).
- Proxy Server: A SIP server that routes SIP requests between clients and other servers. It can enforce policies, provide routing decisions, and support load balancing.
- Registrar Server: Handles SIP REGISTER requests, maintaining a database of registered users and their current locations (IP addresses or endpoints).
- Redirect Server: Provides alternative routing information by responding to requests with the address of the next-hop server or endpoint.
- Location Server: Stores mapping information between SIP addresses (URIs) and physical network addresses, supporting user mobility and session routing.
SIP networks are highly flexible and scalable, supporting a range of deployment scenarios from small office setups to global cloud-based communications platforms.
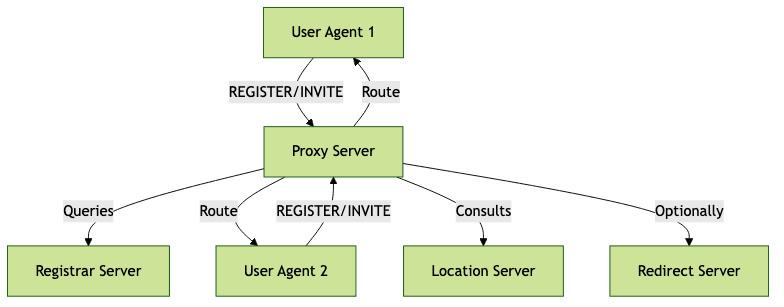
This diagram illustrates the primary SIP network components and their interactions, highlighting how requests traverse the network to enable session initiation and management.
SIP Addresses and Identifiers
A SIP address, or SIP URI (Uniform Resource Identifier), is used to uniquely identify users or resources in a SIP network. The format resembles an email address, such as
sip:alice@example.com. SIP addresses enable seamless routing within and between domains, making user mobility and global communications straightforward within SIP-enabled networks.How SIP Works: Call Flow and Message Exchange
The SIP call flow involves a series of well-defined messages exchanged between endpoints and servers to establish, manage, and terminate sessions. Here’s a step-by-step overview:
- Registration: The user agent sends a REGISTER message to the registrar server to announce its availability.
- Session Initiation: The caller sends an INVITE request (often via a proxy server) to the callee’s SIP address. The INVITE includes session description information (typically using SDP—Session Description Protocol) to negotiate media parameters.
- Session Progress: The callee’s device responds with provisional responses (e.g., 100 Trying, 180 Ringing) and, finally, a 200 OK upon accepting the session.
- Session Confirmation: The caller sends an ACK to confirm receipt of the 200 OK, completing the session setup.
- Media Exchange: Media (voice, video) flows directly between endpoints, typically over RTP.
- Session Termination: Either party can send a BYE message to terminate the session.
A typical SIP INVITE message looks like this:
1INVITE sip:bob@example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Bob <sip:bob@example.com>
5From: Alice <sip:alice@example.com>;tag=1928301774
6Call-ID: a84b4c76e66710
7CSeq: 314159 INVITE
8Contact: <sip:alice@pc33.example.com>
9Content-Type: application/sdp
10Content-Length: 142
11
12v=0
13o=alice 2890844526 2890844526 IN IP4 pc33.example.com
14s=-
15c=IN IP4 pc33.example.com
16t=0 0
17m=audio 49170 RTP/AVP 0
18This message invites Bob to join a voice session and includes session parameters in the SDP.
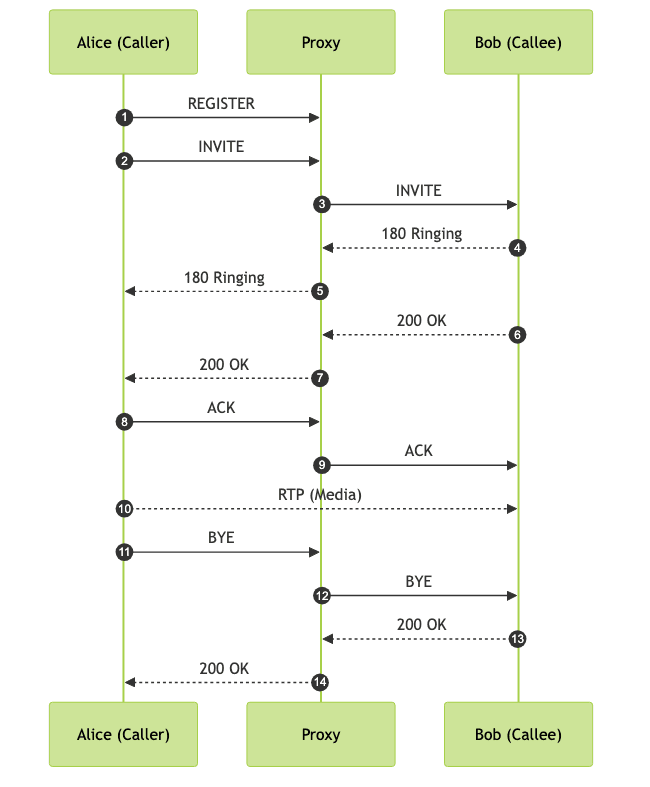
This sequence diagram visualizes the SIP signaling flow between two endpoints, mediated by a proxy server.
SIP vs. Other Networking Protocols
SIP is often compared with other signaling protocols and media transport technologies:
- SIP vs H.323: Both are signaling protocols for multimedia communications. SIP is text-based, modular, and easier to extend, making it more popular for modern IP communications. In contrast, H.323 is binary and complex, with roots in traditional telephony and video conferencing.
- SIP vs RTP: SIP handles signaling (session setup and teardown), while RTP is responsible for the real-time transport of media like voice and video. They are complementary protocols—SIP negotiates session details, RTP streams the actual media.
- SIP vs Traditional Telephony Signaling (SS7): SIP provides greater flexibility, scalability, and integration with Internet services compared to legacy circuit-switched signaling like SS7.
The unique strengths of SIP—open standards, extensibility, and integration with IP—make it the preferred choice for next-generation unified communications and service provider networks.
Benefits and Applications of SIP in Modern Networks
SIP delivers a multitude of benefits for organizations adopting IP-based communications:
- Cost Savings: SIP trunking reduces infrastructure and call costs by leveraging the Internet for voice and video traffic.
- Scalability: Easily supports small startups to large enterprises, with simple scaling from a handful of endpoints to thousands.
- Flexibility: Integrates seamlessly with software applications, mobile devices, and cloud platforms.
- Unified Communications: Enables voice, video, instant messaging, presence, and collaboration tools over a single protocol.
- VoIP and Video Calls: SIP powers popular VoIP and video conferencing solutions, supporting HD audio and video calls globally.
- Disaster Recovery: SIP-based systems are highly resilient, supporting dynamic rerouting and cloud failover.
Use cases include:
- Enterprise VoIP systems
- Video conferencing platforms
- Unified communications suites
- Contact centers
- SIP-enabled mobile and web applications
With robust support for media negotiation, session management, and global addressing, SIP remains the backbone of scalable, modern communication infrastructures in 2025.
Security Considerations in SIP Networking
While SIP offers significant advantages, it also introduces specific security challenges:
- Spoofing: Attackers may impersonate users or servers to redirect calls or intercept sessions.
- Eavesdropping: Unencrypted SIP and RTP traffic can be intercepted, exposing sensitive call content.
- Denial-of-Service (DoS) Attacks: Flooding SIP servers can disrupt communications.
Best practices for securing SIP networks include:
- Enforcing strong authentication (e.g., Digest authentication)
- Using TLS (Transport Layer Security) for SIP signaling encryption
- Employing SRTP (Secure RTP) for media encryption
- Implementing access lists and firewalls to restrict unwanted traffic
- Regularly updating and patching SIP servers and endpoints
Implementing SIP: Practical Considerations
When deploying SIP in your network, consider the following practical aspects:
- Selecting SIP Providers/Equipment: Choose reputable SIP trunk providers and ensure endpoints (phones, softphones, gateways) are compatible with your chosen infrastructure.
- Integration: Assess how SIP will integrate with existing PBX systems, contact centers, and collaboration tools. Use SIP gateways for legacy system interoperability.
- Deployment Tips:
- Test network bandwidth and QoS for media traffic
- Configure NAT traversal (STUN, TURN, ICE) for remote endpoints
- Monitor SIP logs and call quality metrics for proactive troubleshooting
Careful planning and integration ensure a smooth, scalable, and reliable SIP deployment.
Conclusion
Session Initiation Protocol (SIP) is the driving force behind IP-based voice, video, and unified communications in 2025. Its flexible architecture, robust signaling capabilities, and broad industry adoption make it indispensable for modern networking. By understanding SIP’s components, call flows, security considerations, and deployment best practices, developers and IT professionals can build resilient, scalable, and feature-rich communication solutions for the future.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ