Introduction to Real-Time Protocols
Real-time protocols are a set of communication standards designed to facilitate the immediate exchange of data between systems with minimal delay. Unlike traditional protocols that prioritize reliability over speed, real-time protocols focus on delivering data within a strict time constraint. This makes them crucial for applications where timely delivery is paramount, even if it means sacrificing some data integrity.
The Importance of Low Latency and High Throughput
Low latency, the measure of delay in data transmission, and high throughput, the amount of data transferred per unit of time, are the cornerstones of real-time communication. These two factors directly impact the responsiveness and effectiveness of real-time applications. For example, in high-frequency trading, even a millisecond delay can result in significant financial losses. Similarly, in video conferencing or online gaming, low latency ensures a smooth and interactive experience.
Key Characteristics of Real-Time Protocols
Real-time protocols exhibit several key characteristics:
- Low Latency: Minimizing delays is a primary objective.
- High Throughput: Maximizing the amount of data transmitted within a specific time frame.
- Predictability: Maintaining consistent performance and minimizing jitter (variations in latency).
- Prioritization: The ability to prioritize real-time data over other types of traffic.
- Synchronization: Ensuring that data streams are synchronized accurately.
Types of Real-Time Protocols
Numerous real-time protocols exist, each tailored to specific application needs. Here are some of the most prominent:
Real-Time Transport Protocol (RTP)
RTP is a widely used protocol for delivering audio and video over IP networks. It provides end-to-end transport functions suitable for applications transmitting real-time data, such as streaming media and VoIP. RTP typically runs over UDP. It does not inherently provide any mechanisms to ensure timely delivery; however, it is often used in conjunction with the RTP Control Protocol (RTCP), which provides feedback on the quality of service.
RTP Header Structure
1/* RTP Header fields. */
2struct rtp_header {
3 unsigned char cc:4; /* CSRC count */
4 unsigned char x:1; /* header extension flag */
5 unsigned char p:1; /* padding flag */
6 unsigned char v:2; /* version */
7 unsigned char pt:7; /* payload type */
8 unsigned char m:1; /* marker bit */
9 unsigned short seq_no; /* sequence number */
10 unsigned int timestamp; /* timestamp */
11 unsigned int ssrc; /* synchronization source */
12};
13Real-Time Streaming Protocol (RTSP)
RTSP is a network control protocol designed for use in entertainment and communications systems to control streaming media servers. It is used for establishing and controlling media sessions between endpoints. RTSP clients can issue commands like PLAY, PAUSE, and RECORD to control the server. While RTSP controls the stream, the actual media data is typically transported using RTP.
Real-Time Publish-Subscribe (RTPS)
RTPS is a middleware protocol designed for real-time data distribution, particularly in robotics, industrial automation, and defense systems. It follows a publish-subscribe pattern, where publishers send data and subscribers receive only the data they are interested in. RTPS emphasizes reliability, low latency, and scalability. It's a core part of the Data Distribution Service (DDS) standard.
PROFINET RT
PROFINET RT (Real-Time) is an industrial Ethernet protocol used for deterministic communication in automation environments. It enables fast and reliable data exchange between controllers, I/O devices, and other automation components. PROFINET RT focuses on achieving very short cycle times and precise synchronization for demanding industrial applications.
Other Notable Real-Time Protocols
Other real-time protocols include: Session Initiation Protocol (SIP), H.323, and various proprietary protocols used in specific industries.
Choosing the Right Real-Time Protocol
Selecting the most appropriate real-time protocol is crucial for ensuring the success of any real-time application. Several factors must be considered during the decision-making process.
Factors Influencing Protocol Selection
- Application Requirements: The specific needs of the application, such as the type of data being transmitted (audio, video, sensor data), the acceptable level of latency, and the required data integrity, should be carefully considered. For example, high-frequency trading requires protocols with extremely low latency, while streaming video may tolerate slightly higher latency but requires high bandwidth.
- Network Infrastructure: The underlying network infrastructure, including bandwidth, latency, and reliability, will influence the choice of protocol. Some protocols are better suited for lossy networks, while others require a more stable and predictable network environment.
- Scalability Needs: The ability of the protocol to scale to handle a large number of concurrent users or devices is an important consideration. Some protocols are inherently more scalable than others.
- Security Considerations: Security requirements, such as encryption, authentication, and access control, must be addressed. Certain protocols offer built-in security features, while others require additional security measures to be implemented.
Comparing Key Protocols
| Protocol | Latency | Bandwidth Efficiency | Reliability | Complexity |
|---|---|---|---|---|
| RTP | Low | High | Low (relies on UDP or RTCP) | Moderate |
| RTSP | Moderate | Moderate | Moderate | Moderate |
| RTPS | Low | High | High | High |
| PROFINET RT | Very Low | High | High | High |
- Latency: Refers to the delay in data transmission.
- Bandwidth Efficiency: Indicates how efficiently the protocol utilizes network bandwidth.
- Reliability: Measures the protocol's ability to ensure data delivery.
- Complexity: Reflects the ease of implementation and maintenance.
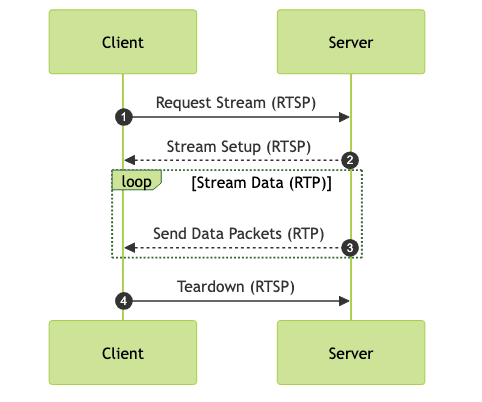
Here's a Mermaid diagram explaining a simplified version of RTP Streaming:
Case Studies: Real-World Applications of Different Protocols
- RTP: Used extensively in video conferencing applications like Zoom and Microsoft Teams.
- RTSP: Employed in IP cameras and video surveillance systems.
- RTPS: Utilized in autonomous vehicles and robotics for real-time data exchange.
- PROFINET RT: Found in industrial automation systems for controlling machinery and processes.
Implementation and Optimization of Real-Time Protocols
Implementing and optimizing real-time protocols requires careful consideration of various factors, including the underlying transport protocol, network conditions, and application requirements.
UDP vs. TCP for Real-Time Communication
UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) are the two primary transport protocols used in real-time communication. UDP is a connectionless protocol that offers low latency but does not guarantee reliable delivery. TCP, on the other hand, is a connection-oriented protocol that provides reliable delivery but introduces higher latency due to its connection establishment and error recovery mechanisms.
For real-time applications that prioritize low latency over reliability, UDP is often the preferred choice. However, for applications that require reliable delivery, TCP may be more suitable, although it may necessitate additional optimization techniques to minimize latency.
Addressing Challenges like Jitter and Packet Loss
Jitter and packet loss are common challenges in real-time communication, particularly over IP networks. Jitter refers to variations in latency, while packet loss occurs when data packets are lost during transmission. These issues can significantly degrade the quality of real-time applications.
- Jitter Buffering Techniques: Jitter buffers are used to smooth out variations in latency by delaying the playback of data. This allows the application to compensate for jitter and provide a more consistent experience.
- Forward Error Correction: FEC techniques add redundant data to the transmitted stream, allowing the receiver to reconstruct lost packets without requiring retransmission. FEC can be effective in mitigating the impact of packet loss, but it also increases bandwidth consumption.
- Congestion Control Mechanisms: Congestion control mechanisms are used to prevent network congestion and reduce packet loss. These mechanisms adjust the transmission rate based on network conditions.
Optimizing Network Configuration for Real-Time Performance
Optimizing network configuration can significantly improve real-time performance. This includes prioritizing real-time traffic using Quality of Service (QoS) mechanisms, minimizing network latency by reducing the number of hops, and ensuring adequate bandwidth availability.
Security Considerations in Real-Time Protocols
Security is a critical aspect of real-time protocols, as vulnerabilities can lead to disruptions, data breaches, and other security incidents.
Vulnerabilities and Threats
Real-time protocols are susceptible to various vulnerabilities and threats, including:
- Denial-of-Service (DoS) Attacks: Overwhelming the system with traffic to prevent legitimate users from accessing it.
- Man-in-the-Middle (MitM) Attacks: Intercepting and manipulating data in transit.
- Data Injection Attacks: Injecting malicious data into the real-time stream.
- Authentication Spoofing: Impersonating a legitimate user or device.
Security Mechanisms
- Encryption: Encrypting data to protect it from unauthorized access.
- Authentication: Verifying the identity of users and devices.
- Access Control: Restricting access to real-time data based on user roles and permissions.
Best Practices for Secure Implementation
- Use strong encryption algorithms.
- Implement robust authentication mechanisms.
- Regularly update security patches.
- Monitor network traffic for suspicious activity.
- Follow security best practices for the underlying operating system and network infrastructure.
Future Trends in Real-Time Protocols
The landscape of real-time protocols is constantly evolving, driven by advancements in networking technology and the emergence of new applications.
The Rise of 5G and its Impact
The advent of 5G technology is poised to revolutionize real-time communication. 5G offers significantly higher bandwidth, lower latency, and increased network capacity compared to previous generations of mobile networks. This will enable new real-time applications, such as augmented reality, virtual reality, and autonomous driving.
Integration with IoT and Edge Computing
The integration of real-time protocols with IoT and edge computing is another significant trend. Edge computing involves processing data closer to the source, reducing latency and improving responsiveness. Real-time protocols are essential for enabling real-time data processing and control in IoT environments.
Conclusion
Real-time protocols are essential for enabling a wide range of applications that require timely and reliable data delivery. By understanding the different types of real-time protocols, their characteristics, and implementation considerations, developers can build high-performance, responsive, and secure real-time systems. As networking technology continues to evolve, real-time protocols will play an increasingly important role in shaping the future of communication and computing.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ