Introduction to STUN Server WebRTC
Web Real-Time Communication (WebRTC) has revolutionized how browsers and native apps enable peer-to-peer connectivity for audio, video, and data sharing. By eliminating the need for plug-ins or proprietary software, WebRTC allows developers to build rich communication applications directly in the browser, unlocking possibilities for video conferencing, file sharing, and real-time collaboration tools.
A fundamental challenge in WebRTC peer-to-peer communication is Network Address Translation (NAT) traversal. Most devices connect to the internet from behind routers or firewalls that obscure their actual IP addresses. This is where the STUN server comes into play. The term "stun server webrtc" refers to a critical service that enables WebRTC clients to discover their public-facing IP and port, allowing peers to establish direct connections even when separated by NAT devices.
The ability to traverse NATs is essential for seamless, low-latency communication. Without NAT traversal, establishing connectivity between peers would often be impossible, especially in complex network topologies. STUN servers are a cornerstone of the WebRTC stack, working alongside protocols like TURN and ICE to ensure robust, reliable connections across diverse environments.
In this guide, we’ll explore how STUN servers work, how to set them up (using open source solutions like coturn), their configuration, and best practices for optimizing NAT traversal in WebRTC applications. Whether you’re building a video chat app, multiplayer game, or collaborative platform, understanding STUN server WebRTC integration is vital for delivering reliable real-time experiences.
How STUN Servers Work in WebRTC
STUN (Session Traversal Utilities for NAT), standardized in RFC 5389, provides a lightweight protocol for NAT traversal. In the context of WebRTC, a STUN server enables clients to determine their public IP address and port as seen by external networks. This information is crucial for establishing direct peer-to-peer communication channels across NATs and firewalls.
When a WebRTC client initiates a connection, it sends a STUN binding request to the server via UDP (and optionally TCP). The STUN server responds with the public IP and port from which the request originated. This process allows the client to advertise its reachable address to peers, even if it resides behind a NAT device.
STUN Server Interaction Workflow
To visualize the flow, consider the following Mermaid diagram:
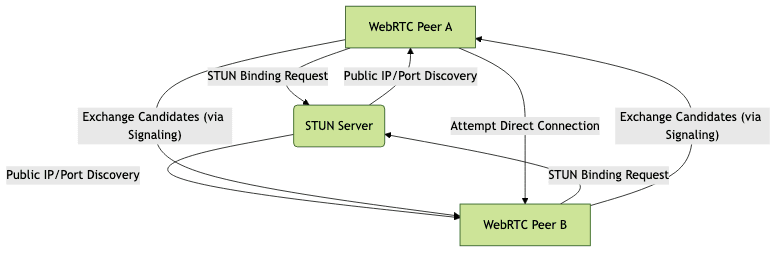
This sequence demonstrates how both peers use the STUN server to discover their public addresses. The signaling channel (outside the scope of STUN) then facilitates the exchange of this information, enabling peers to attempt a direct connection.
STUN is stateless and lightweight, making it suitable for high-scale deployments. However, its effectiveness depends on the NAT type—symmetric NATs, for example, may require additional solutions like TURN for successful connectivity.
STUN vs TURN for WebRTC
While STUN servers facilitate discovery of public endpoints, they cannot always guarantee connectivity, especially in restrictive network environments. This is where TURN (Traversal Using Relays around NAT) becomes essential. Unlike STUN, which only helps peers discover their public IP, TURN servers act as relay intermediaries, forwarding media between clients when direct peer-to-peer communication fails.
Key differences:
- STUN: Used for public IP discovery; enables direct connectivity when possible; lightweight and efficient; fails with symmetric NAT or strict firewalls.
- TURN: Acts as a relay server; always works regardless of NAT type but introduces additional latency and bandwidth costs.
The ICE (Interactive Connectivity Establishment) protocol orchestrates the process of gathering candidates via STUN and TURN, testing which path—direct or relayed—should be used for optimal connectivity. In most WebRTC scenarios, ICE first attempts STUN-based direct connections, falling back to TURN only if needed.
Setting Up a STUN Server for WebRTC
Choosing the right STUN server for your WebRTC deployment is crucial. Popular open-source options include coturn and STUNTMAN, both supporting STUN and TURN protocols. Alternatively, you can use public STUN servers, but for production environments, deploying a private instance offers greater reliability and security.
Prerequisites
- Ubuntu Linux server (or similar)
- Root or sudo privileges
- Open network ports (typically UDP 3478)
Installing coturn on Ubuntu
1sudo apt update
2sudo apt install coturn
3Basic coturn Configuration
Edit the
/etc/turnserver.conf file to enable STUN functionality. Here’s a minimal example:1listening-port=3478
2fingerprint
3lt-cred-mech
4user=webrtcuser:strongpassword
5realm=example.com
6log-file=/var/log/turnserver.log
7simple-log
8no-stdout-log
9listening-port: Default is 3478 for STUN/TURN over UDP/TCPuserandlt-cred-mech: Enable authentication for TURN (optional for pure STUN)realm: Used for authenticationlog-file: Path to log output
Running coturn
1sudo turnserver -c /etc/turnserver.conf
2Firewall and Network Configuration
Ensure that UDP (and optionally TCP) port 3478 is open on your server’s firewall:
1sudo ufw allow 3478/udp
2sudo ufw allow 3478/tcp
3Security Best Practices
- Use strong credentials if enabling TURN/relay functionality
- Restrict access to known IP ranges when possible
- Monitor logs for unauthorized access attempts
- Regularly update coturn or your chosen STUN server software
Setting up a private STUN server gives you full control over configuration, security, and logging—key for enterprise or privacy-focused applications.
Using Public vs Private STUN Servers
Many developers use public STUN servers for convenience. Here are some well-known public options:
stun.l.google.com:19302stun1.l.google.com:19302stun2.l.google.com:19302stun.stunprotocol.org:3478
Pros and Cons
Public STUN Servers:
- Pros: Easy to use, no setup required
- Cons: No guarantee of availability, limited support, potential rate limiting, possible security/privacy concerns
Private STUN Servers:
- Pros: Full control, improved reliability, customizable security and logging
- Cons: Requires setup and maintenance, infrastructure costs
For mission-critical or high-volume applications, deploying a private STUN server is recommended to ensure reliability, privacy, and compliance with organizational policies.
Integrating STUN Servers with WebRTC Applications
To enable NAT traversal, WebRTC applications must be configured with one or more STUN servers. This is accomplished via the
iceServers property in the RTCPeerConnection API.Example: JavaScript WebRTC Client Configuration
1const peerConnection = new RTCPeerConnection({
2 iceServers: [
3 { urls: "stun:stun.l.google.com:19302" },
4 // Add TURN server here if needed
5 ]
6});
7You can also specify your private STUN server:
1const peerConnection = new RTCPeerConnection({
2 iceServers: [
3 { urls: "stun:your-stun-server.example.com:3478" }
4 ]
5});
6Troubleshooting Connectivity Issues
If peers fail to connect, consider the following:
- Firewall: Ensure necessary UDP/TCP ports are open
- NAT Type: Symmetric NATs may block STUN-based direct connectivity (consider TURN)
- Server Reachability: Verify that your STUN server is accessible from client networks
- Logging: Enable verbose logging in coturn or your chosen server for diagnostics
Proper configuration and network planning are essential to minimize connectivity issues in production environments.
Advanced Topics: Network Topology, NAT Types, and ICE
NAT devices come in various types—full cone, restricted cone, port-restricted cone, and symmetric. STUN is highly effective with cone NATs but struggles with symmetric NATs, where the mapping of internal to external addresses depends on the destination. This is why the ICE protocol is crucial in WebRTC.
ICE gathers multiple candidate addresses using STUN (for server-reflexive candidates), TURN (for relayed candidates), and local interfaces. It then prioritizes and tests these candidates to find the best working path.
ICE Candidate Gathering (Mermaid Diagram)
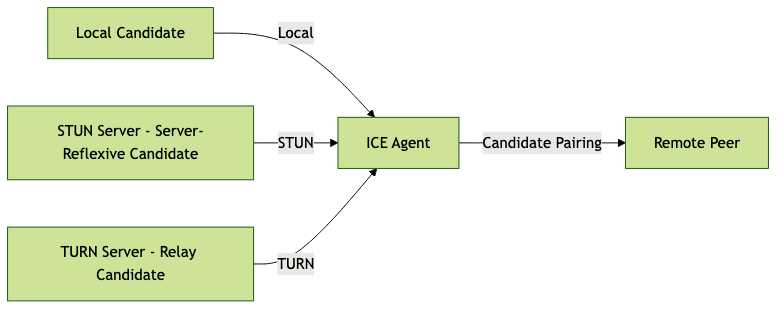
This diagram shows how the ICE agent aggregates candidates from various sources to maximize connection success, adapting to differing network topologies and NAT types.
Best Practices and Common Pitfalls
- Always provide fallback TURN servers alongside STUN for maximum reliability
- Limit the number of STUN requests to avoid rate limiting
- Regularly monitor and update your STUN/TURN servers
- Avoid exposing unnecessary ports or weak credentials
- Test connectivity with various NAT types during development
Misconfigurations, such as incorrect port settings or weak authentication, are common pitfalls that can severely impact WebRTC connectivity.
Conclusion
STUN servers are foundational to effective NAT traversal in WebRTC, enabling direct, low-latency peer-to-peer communication. By leveraging open-source solutions like coturn, observing security best practices, and integrating with ICE, developers can ensure robust connectivity across diverse network environments. For mission-critical applications, a private STUN deployment is often the best choice. Mastering STUN server WebRTC integration is key to building high-performance, reliable real-time applications.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ