Introduction to the SIPS Protocol
The SIPS protocol (Session Initiation Protocol Secure) is a standardized communication protocol that brings robust security and structure to signaling in IP-based networks. Built as an extension of the widely used SIP (Session Initiation Protocol), the SIPS protocol introduces encrypted transport layers to protect signaling messages from interception and tampering.
In a world where data breaches and cyber threats are increasingly common, the need for secure, structured protocols like SIPS is paramount. From VoIP telephony to complex distributed systems, SIPS ensures that signaling data is transmitted over secure channels, providing integrity and confidentiality. As we move into 2025, the SIPS protocol remains a cornerstone for secure, standards-based network communication.
SIP vs SIPS: Understanding the Difference
SIP (Session Initiation Protocol) is a foundational protocol in modern telephony and multimedia sessions, enabling call setup, management, and teardown in IP networks. However, by default, SIP does not encrypt its signaling traffic, leaving it vulnerable to eavesdropping and attacks.
The SIPS protocol enhances SIP by mandating the use of TLS (Transport Layer Security) for all signaling traffic. This ensures that every hop between SIP entities is encrypted, greatly reducing risk and meeting compliance requirements. Practical implications are major: SIPS is now a baseline for secure VoIP deployments, regulatory compliance, and encrypted communications in enterprise environments.
Communication Flow: SIP vs SIPS
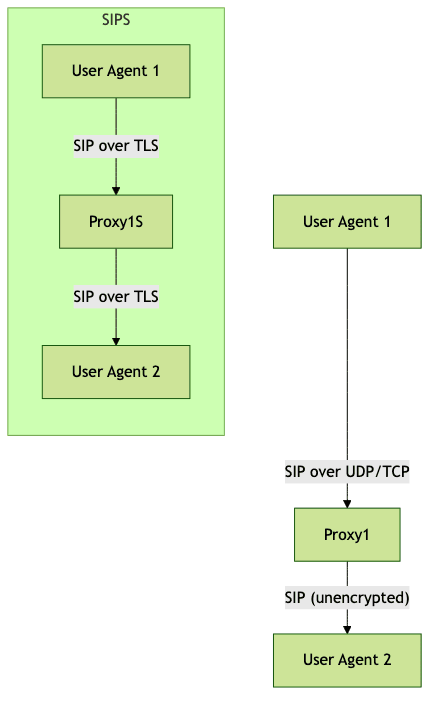
As shown above, SIP typically operates over UDP or TCP, while SIPS enforces encrypted TLS channels at every hop. This distinction is critical for regulatory, privacy, and operational reasons.
Core Components of the SIPS Protocol
SIP Transport Protocols
The SIPS protocol leverages several transport layers to transmit signaling messages. Traditional SIP uses UDP (User Datagram Protocol) and TCP (Transmission Control Protocol). SIPS, however, requires TLS—ensuring all communication is encrypted, authenticated, and tamper-proof. This makes SIPS the preferred choice for environments demanding stringent security.
Encryption and Security Features
TLS (Transport Layer Security) is at the heart of the SIPS protocol’s security model. TLS encrypts SIP signaling data, provides mutual authentication, and prevents man-in-the-middle attacks. This is crucial for safeguarding sensitive call information and ensuring compliance with modern security standards.
SIPS Configuration Example
1# SIPS configuration for Asterisk (sip.conf)
2[general]
3enable=yes
4tlsenable=yes
5tlsbindaddr=0.0.0.0:5061
6tlsclientmethod=tlsv1_2
7tlscafile=/etc/asterisk/keys/ca.crt
8tlscrtfile=/etc/asterisk/keys/server.crt
9tlskeyfile=/etc/asterisk/keys/server.key
10tlsverifyclient=yes
11This configuration ensures Asterisk only accepts SIPS connections using strong TLS encryption.
Protocol Standards and Documentation
The SIPS protocol is defined and maintained through rigorous documentation and improvement proposal processes. Communities and standards bodies like the IETF (Internet Engineering Task Force) use formal proposals (such as SIP, SIPS, and NIPs) to evolve protocol features. Documentation ensures interoperability and provides a reference for secure, standardized implementations. For protocol documentation, see the
IETF SIP RFC 3261
andRFC 5630 for SIPS
.The SIPS Protocol Process: From Proposal to Implementation
What is an Improvement Proposal?
An improvement proposal is a formal process used by technical communities to suggest, discuss, and adopt changes or enhancements to a protocol or system like SIPS. This community-driven approach ensures transparency, peer review, and open participation in evolving the protocol.
SIPS Proposal Lifecycle
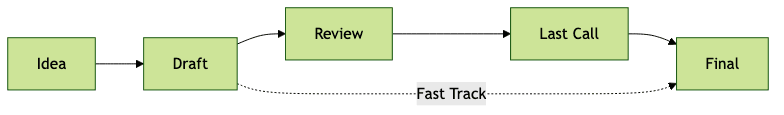
The SIPS protocol follows a structured lifecycle for proposals:
- Idea: Anyone in the community can suggest an improvement.
- Draft: The idea is formalized into a proposal document.
- Review: The draft is openly reviewed and discussed by the community.
- Last Call: Final comments are solicited before closure.
- Final: The proposal is accepted, published, and implemented.
A fast track option exists for urgent security fixes or minor updates, allowing expedited community review.
SIPS Proposal Workflow Diagram
Role of Community and Collaboration
Collaboration is key to the SIPS protocol’s evolution. Developers, architects, and security experts participate in forums, GitHub repositories, and open mailing lists, contributing code, reviews, and feedback. Open collaboration ensures the protocol remains secure, relevant, and widely adopted.
Implementing the SIPS Protocol: Best Practices and Code Examples
SIPS Configuration and Deployment
Implementing the SIPS protocol involves several critical steps:
- Obtain valid TLS certificates from a trusted certificate authority (CA).
- Configure SIP servers (e.g., Asterisk, Kamailio, FreeSWITCH) to only accept SIPS (TLS) connections.
- Enforce strong cipher suites and disable insecure protocols.
- Regularly update server software and TLS libraries.
Secure SIPS Server Setup Example (Asterisk)
1[general]
2tlsenable=yes
3tlsbindaddr=0.0.0.0:5061
4tlsclientmethod=tlsv1_2
5tlscafile=/etc/asterisk/keys/ca.crt
6tlscrtfile=/etc/asterisk/keys/server.crt
7tlskeyfile=/etc/asterisk/keys/server.key
8tlsverifyclient=yes
9transport=tls
10This setup forces all SIP signaling to use TLS, ensuring encrypted and authenticated communication.
Common Pitfalls and Troubleshooting
While deploying the SIPS protocol, common issues include:
- Misconfigured certificates or expired keys
- Incompatible TLS versions between clients and servers
- Firewall or NAT issues blocking port 5061 (default for SIPS)
- Legacy endpoints that do not support SIPS
Careful validation, regular audits, and staged rollouts can mitigate these pitfalls.
Interoperability and Compliance
The SIPS protocol is designed to interoperate with existing SIP, RTP (Real-time Transport Protocol), and other telephony standards. Compliance with RFCs and industry best practices ensures seamless integration across devices, networks, and vendors. Testing with tools like
SIPp
and cross-vendor certification are recommended for robust deployments.SIPS Protocol in Different Domains
SIPS in Telephony and VoIP
The SIPS protocol is widely used in telephony and VoIP environments to establish secure, encrypted signaling channels for calls, video, and messaging. Benefits include:
- Protection against eavesdropping and impersonation
- Compliance with regulatory requirements (GDPR, HIPAA, etc.)
- Enhanced trust for users and partners
SIPS for Blockchain and Decentralized Platforms
In blockchain ecosystems, improvement proposals (sometimes called SIPS, SIPs, or NIPs) are used to define protocol upgrades and security enhancements. Examples include Sui Improvement Proposals and Symblox Improvement Proposals, which leverage open collaboration and formal documentation to guide secure protocol evolution.
SIPS for Digital Archiving
Protocols inspired by SIPS concepts are used in digital archiving systems like OAIS and CLOCKSS, ensuring secure, standardized communication for long-term data preservation and integrity.
Future of the SIPS Protocol and Emerging Trends
Looking ahead to 2025 and beyond, the SIPS protocol continues to evolve. Ongoing developments include:
- Integration of post-quantum cryptography for future-proof security
- Automated certificate management (ACME, Let's Encrypt)
- Enhanced interoperability with decentralized and cloud-native platforms
- Community-driven adoption of new features via transparent improvement proposal processes
Continued community participation, rigorous peer review, and adherence to best practices ensure the SIPS protocol remains relevant and secure as the technological landscape shifts.
Conclusion: Why SIPS Protocol Matters
The SIPS protocol is more than just an encrypted transport for SIP—it is a vital, community-driven standard that underpins secure, structured communication in modern networks. By adopting SIPS, organizations and developers ensure confidentiality, integrity, and interoperability. Get involved in the SIPS community to help shape the secure communication standards of tomorrow.
Authoritative Links:
IETF SIP RFC 3261
– Official SIP protocol specificationRFC 5630: The SIPS URI Scheme
– SIPS protocol technical detailsSIPp: SIP Testing Tool
– Open source SIP and SIPS testing
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ